Einführung
In der Automobilindustrie spielen die Konzepte der Hardware-Sicherheitsmodule (HSMs), der Hardware-Sicherheits-Engines (HSEs) und der sicheren Hardware-Erweiterungen (SHEs) eine zentrale Rolle bei der Gewährleistung der Sicherheit und Integrität kritischer Systeme und sensibler Daten. Obwohl diese Technologien das gemeinsame Ziel haben, die Sicherheit zu verbessern, unterscheiden sich ihre Anwendungen und Funktionalitäten erheblich. In diesem Fachartikel werden die Unterschiede zwischen HSMs, HSEs und SHEs im Kontext des Automobilsektors untersucht und ihre spezifischen Implementierungen und Vorteile beleuchtet.
Hardware-Sicherheitsmodul (HSM)
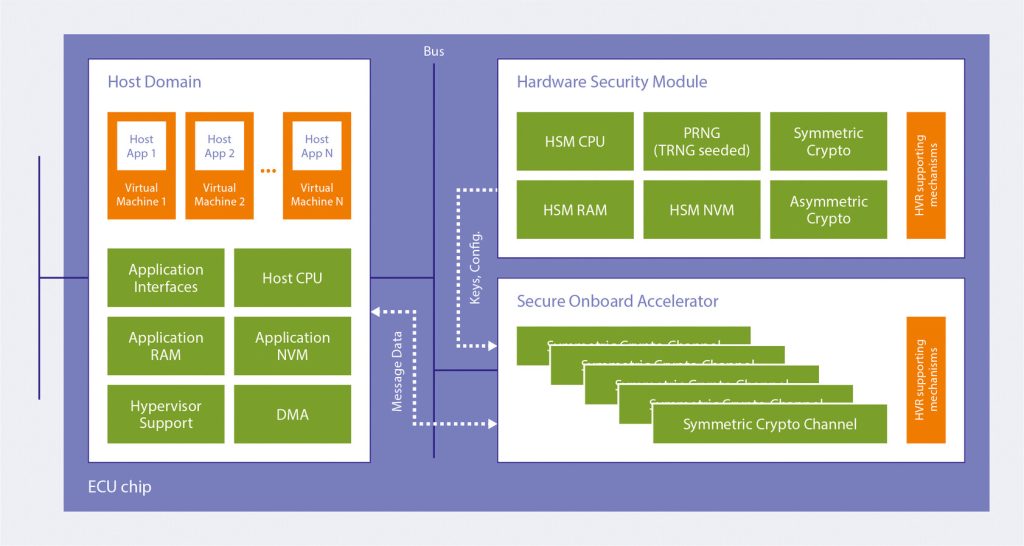
n der Automobilindustrie dient ein Hardware-Sicherheitsmodul (HSM) als spezielles kryptografisches Gerät, das die Sicherheit in verschiedenen Aspekten von Automobilsystemen erhöhen soll. HSMs werden eingesetzt, um sensible Informationen zu schützen, eine sichere Kommunikation zu ermöglichen und die Integrität kritischer Vorgänge in vernetzten Fahrzeugen zu gewährleisten. Sie bieten robuste Sicherheitsmechanismen und Schlüsselverwaltungsfunktionen, um die besonderen Herausforderungen der Automobilindustrie zu bewältigen, wie z. B. die Sicherung der Fahrzeug-zu-Fahrzeug-Kommunikation, den Schutz von Firmware-Updates und die Gewährleistung einer vertrauenswürdigen Softwareausführung.
Schlüsselanwendungen von HSMs in der Automobilindustrie:
- Sichere Kommunikation: HSMs ermöglichen sichere Kommunikationskanäle zwischen elektronischen Steuergeräten (ECUs) innerhalb des Fahrzeugs und gewährleisten Vertraulichkeit, Integrität und Authentifizierung der Datenübertragung. Dies umfasst sichere Nachrichtenprotokolle, sicheren Fernzugriff und sichere Fahrzeug-Infrastruktur-Kommunikation.
- Firmware-Aktualisierungen: HSMs spielen eine entscheidende Rolle bei der Sicherung von Over-The-Air (OTA)-Software-Updates für Kfz-Systeme. Sie authentifizieren die Firmware-Updates, überprüfen ihre Integrität und stellen sicher, dass nur vertrauenswürdige und autorisierte Software auf dem Fahrzeug installiert wird, um unbefugte Änderungen und mögliche Schwachstellen zu verhindern.
- Schlüsselverwaltung: HSMs speichern sicher kryptografische Schlüssel, die für verschiedene Zwecke verwendet werden, z. B. Fahrzeugzugang, Authentifizierung, Verschlüsselung und digitale Signaturen. Sie schützen diese Schlüssel vor unbefugtem Zugriff und bieten sichere Schlüsselbereitstellungsmechanismen.
Hardware-Sicherheitsmodul (HSE)
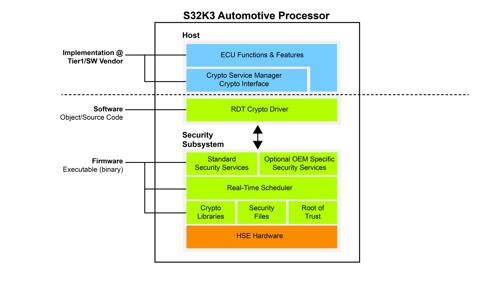
In der Automobilindustrie bezeichnet eine Hardware Security Engine (HSE) eine spezialisierte Hardwarekomponente, die in Fahrzeugsysteme integriert wird, um kryptografische Operationen zu beschleunigen und so die Sicherheit und Leistung zu erhöhen. HSEs sind so konzipiert, dass sie rechenintensive kryptografische Aufgaben vom Hauptprozessor auslagern und so effiziente und sichere kryptografische Operationen gewährleisten, ohne die Systemleistung zu beeinträchtigen.
Schlüsselanwendungen von HSE in der Automobilindustrie
Sichere Kommunikationsprotokolle: HSEs beschleunigen die kryptografischen Operationen, die in sicheren Kommunikationsprotokollen wie Transport Layer Security (TLS) und Secure Sockets Layer (SSL) verwendet werden. Dies gewährleistet eine schnelle und effiziente Ver- und Entschlüsselung von Daten bei der sicheren Datenübertragung zwischen dem Fahrzeug und externen Stellen.
Digitale Signaturen: HSEs bieten Hardware-Beschleunigung für die Erzeugung und Überprüfung digitaler Signaturen. Dies ermöglicht die Authentifizierung und Integritätsprüfung von Daten und gewährleistet, dass Nachrichten oder Softwarekomponenten aus vertrauenswürdigen Quellen stammen und nicht manipuliert wurden.
Sichere Speicherung: HSEs bieten hardwarebasierte sichere Speichermöglichkeiten, die es Automobilsystemen ermöglichen, Verschlüsselungsschlüssel, Zertifikate und sensible Daten sicher zu speichern. Dies schützt vor unbefugtem Zugriff, Diebstahl oder Manipulation wichtiger Informationen.
Unterstützung für hardwarebeschleunigte sichere Boot-Prozesse, um eine vertrauenswürdige und fälschungssichere Software-Ausführung zu gewährleisten.
Sichere Hardware-Erweiterung (SHE)
Sichere Hardware-Erweiterungen (SHEs) in der Automobilindustrie beziehen sich auf integrierte Sicherheitsfunktionen oder Module in Mikrocontrollern oder System-on-Chip (SoC)-Bauteilen. SHEs bieten hardwarebasierte Sicherheitsfunktionen, um die allgemeine Sicherheitslage von Automobilsystemen zu verbessern. Zu diesen Funktionen gehören sichere Boot-Prozesse, sichere Speicherung von Verschlüsselungsschlüsseln, Mechanismen zur Erkennung von Manipulationen und sichere Debug-Schnittstellen. SHEs tragen dazu bei, die Integrität und Vertraulichkeit kritischer Funktionen in Automobilsystemen zu gewährleisten und sie vor potenziellen Angriffen zu schützen.
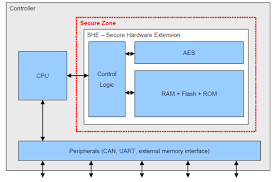
Schlüsselanwendungen von SHEs in der Automobilindustrie:
- Sichere Boot-Prozesse: SHEs ermöglichen sichere Boot-Prozesse, um die Authentizität und Integrität der Software während des Starts des Fahrzeugs zu überprüfen. Dadurch wird sichergestellt, dass nur vertrauenswürdige und überprüfte Softwarekomponenten ausgeführt werden, wodurch das Risiko der Ausführung von bösartigem oder nicht autorisiertem Code verringert wird.
- Sichere Speicherung: SHEs bieten sichere Speichermechanismen für kryptografische Schlüssel, sensible Daten und sichere Firmware-Updates. Dies schützt vor unbefugtem Zugriff, Manipulation oder Extraktion wichtiger Informationen aus dem Fahrzeug.
- Erkennung von Manipulationen und Reaktion darauf: SGU verfügen über Mechanismen zur Erkennung von Manipulationen, um physische Angriffe oder unbefugte Versuche, kritische Systemkomponenten zu manipulieren oder auf sie zuzugreifen, zu erkennen. Diese Mechanismen lösen geeignete Reaktionen aus, z. B. die Deaktivierung bestimmter Funktionen oder die Einleitung von Sicherheitsprotokollen, um potenzielle Bedrohungen zu entschärfen.
- Sichere Debug-Schnittstellen: SHEs bieten sichere Debug-Schnittstellen, die den unbefugten Zugriff auf kritische Systemressourcen während Debugging- oder Wartungsaktivitäten verhindern. Dadurch wird sichergestellt, dass nur autorisierte Stellen auf sensible Komponenten des Fahrzeugsystems zugreifen und mit ihnen interagieren können.
Schlussfolgerung
In der Automobilindustrie dienen Hardware-Sicherheitsmodule (HSMs), Hardware-Sicherheits-Engines (HSEs) und sichere Hardware-Erweiterungen (SHEs) unterschiedlichen, aber sich ergänzenden Zwecken, um die Sicherheit und Integrität kritischer Systeme und sensibler Daten zu verbessern. HSMs gewährleisten eine sichere Schlüsselverwaltung, kryptografische Operationen und den Schutz sensibler Daten. HSEs bieten hardwarebeschleunigte kryptografische Funktionen zur Verbesserung der Systemleistung bei gleichzeitiger Aufrechterhaltung der Sicherheit. SHEs bieten hardwarebasierte Sicherheitsfunktionen, wie z. B. sichere Boot-Prozesse, sichere Speicherung, Manipulationserkennung und sichere Debug-Schnittstellen, um vor potenziellen Angriffen zu schützen und die Integrität von Automobilsystemen zu gewährleisten. Das Verständnis dieser Unterschiede ist für Automobilhersteller und -entwickler von entscheidender Bedeutung, um robuste Sicherheitsmaßnahmen zu implementieren, die auf die besonderen Anforderungen der Automobilindustrie zugeschnitten sind.


