Request Demo
ThreatZ
Cyber Security Management System for Automotive Suppliers (CSMS)
AI-Driven Automotive CSMS covers UNCE R155
ThreatZ is a state-of-the-art cybersecurity management platform designed specifically for the automotive industry. Built to address the evolving threat landscape and complex compliance requirements, ThreatZ provides automotive OEMs, Tier-1 suppliers, and security teams with a comprehensive suite of tools to model, assess, mitigate, and monitor cybersecurity risks throughout the vehicle lifecycle. This document outlines how ThreatZ addresses critical industry challenges, describes its powerful modular architecture, and demonstrates how it enables organizations to achieve and maintain compliance with key standards, including ISO/SAE 21434 and UNECE R155.
Automotive Cybersecurity Challenge
Modern vehicles have evolved into complex networks of connected software and hardware components, creating an expanded attack surface that traditional security approaches struggle to protect. With up to 150 electronic control units and millions of lines of code in a single vehicle, automotive manufacturers and suppliers face unprecedented challenges:
Growing Attack Surface
Connected vehicles introduce multiple entry points for attackers, including wireless interfaces, telematics systems, infotainment units, and third-party applications. As vehicle connectivity increases, so does vulnerability to remote attacks that can compromise critical safety systems.
Complex Supply Chains
The automotive supply chain involves numerous tier suppliers providing components with varying security maturity levels. Managing security across this distributed network creates significant visibility and governance challenges.
Regulatory Pressures
The introduction of UNECE R155/R156 regulations and ISO/SAE 21434 standards has created mandatory cybersecurity requirements for vehicle type approval in many markets. Non-compliance can prevent vehicle sales and damage brand reputation.
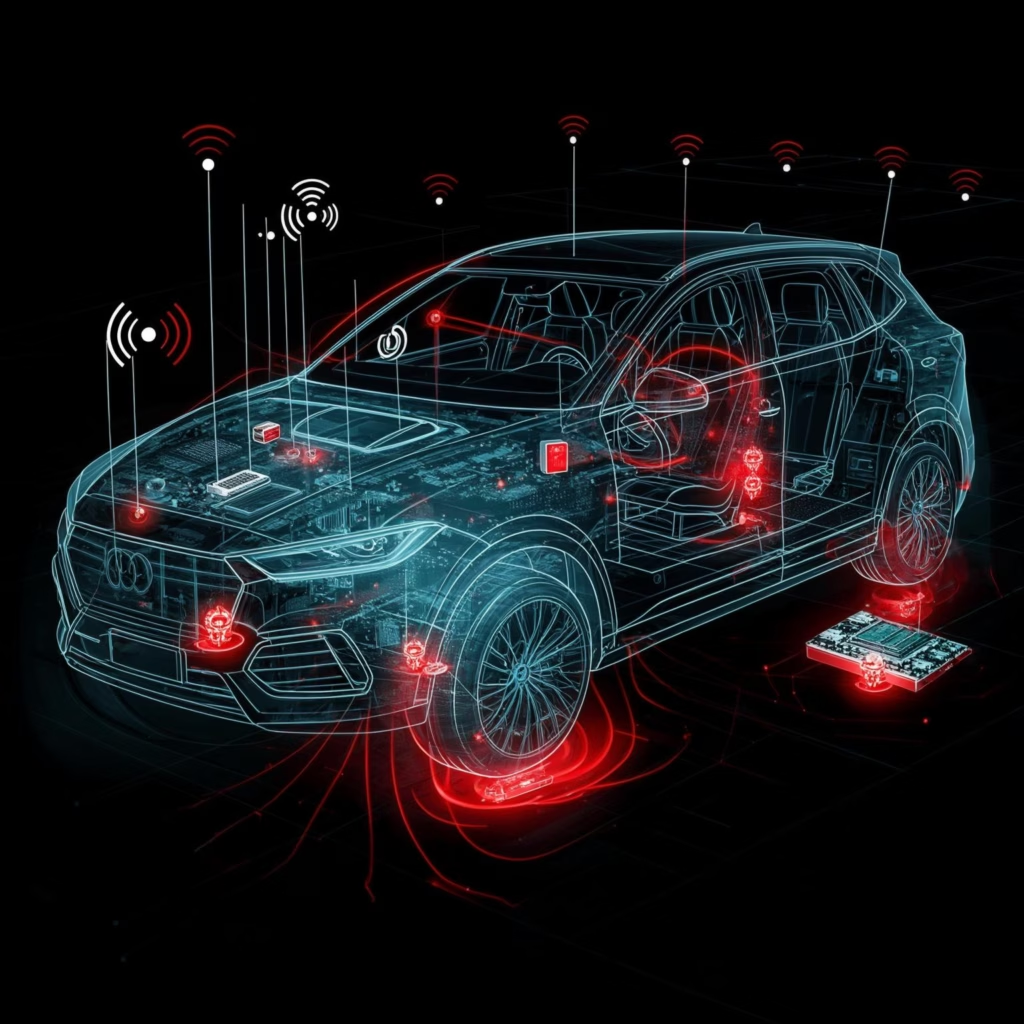
Modern vehicles have evolved into complex networks of connected software and hardware components, creating an expanded attack surface that traditional security approaches struggle to protect. With up to 150 electronic control units and millions of lines of code in a single vehicle, automotive manufacturers and suppliers face unprecedented challenges:
ThreatZ Platform Overview
ThreatZ delivers a comprehensive, integrated approach to automotive cybersecurity management. Built on a modular architecture with a modern tech stack, the platform streamlines all aspects of cybersecurity risk management across the vehicle development lifecycle.
Project Initialization
Define vehicle systems, components, and security goals through structured assessment frameworks aligned with ISO/SAE 21434.
Threat Analysis
Identify, categorize and evaluate potential attack vectors and vulnerabilities using built-in threat intelligence and AI-powered recommendations.
Risk Assessment
Calculate and visualize risk metrics based on attack potential, impact severity, and exploitability factors.
Mitigation Planning
Develop and implement countermeasures, security controls, and verification methods to address identified risks.
Validation & Compliance
Test security controls, generate compliance evidence, and maintain a living cybersecurity management system throughout the vehicle lifecycle.
Vulnerability & Incidents tracking
Continuously monitor and document vulnerabilities and security incidents.
ThreatZ’s intuitive interface allows cybersecurity teams to navigate complex security workflows while maintaining complete traceability. The platform’s AI Assistant provides contextual recommendations, helping teams identify threats, develop mitigation strategies, and implement requirements according to industry best practices from Auto-ISAC and other authoritative sources.
Core Platform Modules
Projects & Assessments
Centralized project management with configurable assessment frameworks. Define system boundaries, components, and security parameters. Track progress with built-in dashboards and compliance metrics.
System Modeling
Create detailed system architecture models with component relationships, data flows, and trust boundaries. Map components to security requirements and threat scenarios.
Threat Modeling
Identify potential attack vectors using built-in threat libraries aligned with STRIDE, TARA, and automotive-specific threat taxonomies. AI-powered recommendations suggest relevant threats based on system architecture.
Validation & Compliance
Plan and execute security tests with comprehensive test case management. Link test results to requirements and maintain evidence for compliance demonstration.
Risk Treatment & Goals
Define cybersecurity goals, requirements, and controls mapped to identified risks. Track mitigation status and verification evidence throughout the development lifecycle.
Risk Assessment
Evaluate and prioritize risks based on customizable risk methodologies. Calculate attack feasibility, impact severity, and overall risk scores with automated inheritance across dependent components.
SBOM & Supply Chain
Manage software bill of materials with component inventory, vulnerability tracking, and dependency visualization. Monitor third-party components for emerging vulnerabilities and compliance issues.
Monitoring & Incidents
Track security incidents, vulnerability reports, and patch management across the vehicle fleet. Implement structured response workflows with full audit trails.
Reports & Compliance
Generate comprehensive documentation and evidence packages for regulatory submission. Export customizable reports for various stakeholders and compliance frameworks.
Policy Manager
Enforce your security governance with customizable policies — define approved actions, license rules, risk treatments, and compliance thresholds within your CSMS.
Security Catalog
Maintain libraries of security requirements, controls, and organizational policies. Ensure consistency across projects with centralized security knowledge management.
AI-Powered Security Intelligence
Contextual Threat Analysis
The AI engine analyzes system components, connections, and functions to automatically identify relevant threats from extensive knowledge bases. By understanding the specific context of each automotive system, it highlights the most probable attack vectors and vulnerabilities that human analysts might overlook.
Mitigation Recommendations
When threats are identified, the AI Assistant suggests appropriate countermeasures and security controls based on industry best practices, Auto-ISAC recommendations, and successful patterns from similar systems. Each recommendation includes implementation guidance and verification approaches.
Requirements Generation
The platform can automatically generate structured security requirements aligned with ISO/SAE 21434 and other standards. These requirements are traceable to threats and risks, ensuring comprehensive coverage of security concerns while maintaining compliance with regulatory frameworks.
Interactive Security Chatbot
Teams can engage with the AI Assistant in natural language to query project context, security best practices, or compliance requirements. This conversational interface provides immediate access to security knowledge without requiring deep expertise in specific standards or methodologies.
ThreatZ integrates advanced artificial intelligence capabilities that transform how security teams approach threat identification, risk assessment, and mitigation planning. The AI Assistant serves as a virtual security expert, available across all platform modules.
By incorporating AI capabilities, ThreatZ significantly reduces the time required for comprehensive security analysis while improving the quality and consistency of security measures across projects. The system continuously learns from new threats and mitigations, ensuring that security knowledge remains current in the rapidly evolving automotive cybersecurity landscape.
Standard Compliance & Regulatory Alignment
ThreatZ is purpose-built to support automotive organizations in achieving and maintaining compliance with critical industry standards and regulations. The platform’s structure and workflows closely align with regulatory requirements, streamlining the path to certification and type approval.
ISO/SAE 21434
ThreatZ implements the complete Cybersecurity Engineering framework defined in ISO/SAE 21434, supporting all phases from concept through decommissioning. The platform’s structure follows the standard’s clauses and work products, ensuring proper documentation and evidence generation for each required activity.
UNECE R155/R156
UNECE R155/R156
Built-in workflows and reports specifically address the Cybersecurity Management System (CSMS) and Software Update Management System (SUMS) requirements mandated by UNECE regulations. ThreatZ helps organizations prepare for and maintain type approval certification through comprehensive evidence packages and audit support.
The platform’s traceability engine ensures that every threat, risk, requirement, and test is properly linked, providing clear evidence of compliance for auditors and certification bodies. Automated gap analysis tools continuously evaluate project maturity against regulatory requirements, highlighting areas that need additional attention before certification submissions.
Deployment Options
Cloud SaaS
Fully managed deployment with automatic updates, scalable resources, and enterprise-grade security. Ideal for organizations looking to minimize infrastructure management.
Private Cloud
Dedicated instance within customer-controlled cloud environment, offering enhanced data sovereignty while maintaining managed service benefits.
On-Premises
Deployment within customer's data center for organizations with strict data residence requirements or air-gapped development environments.
Business Impact & Value Proposition
Licence Types
TARA
The TARA (Threat Analysis and Risk Assessment) License provides comprehensive system and threat modeling capabilities that align with ISO 21434 cybersecurity standards for road vehicles.
Get One-PageBOM & Supply-Chain
The BOM & Supply Chain License combines functions for managing software components, vulnerabilities, licenses, and supplier relationships in a cohesive ecosystem.
Get One-PagerOperations Services
The Operations module of the ThreatZ Cybersecurity Platform provides comprehensive incident management capabilities, real-time monitoring, and advanced threat intelligence integration.
Get One-PageFoundation
Fpindation License provides organizations with the fundamental building blocks needed to establish a robust cybersecurity management system through security governance, threat management, and compliance reporting.
Get One-Page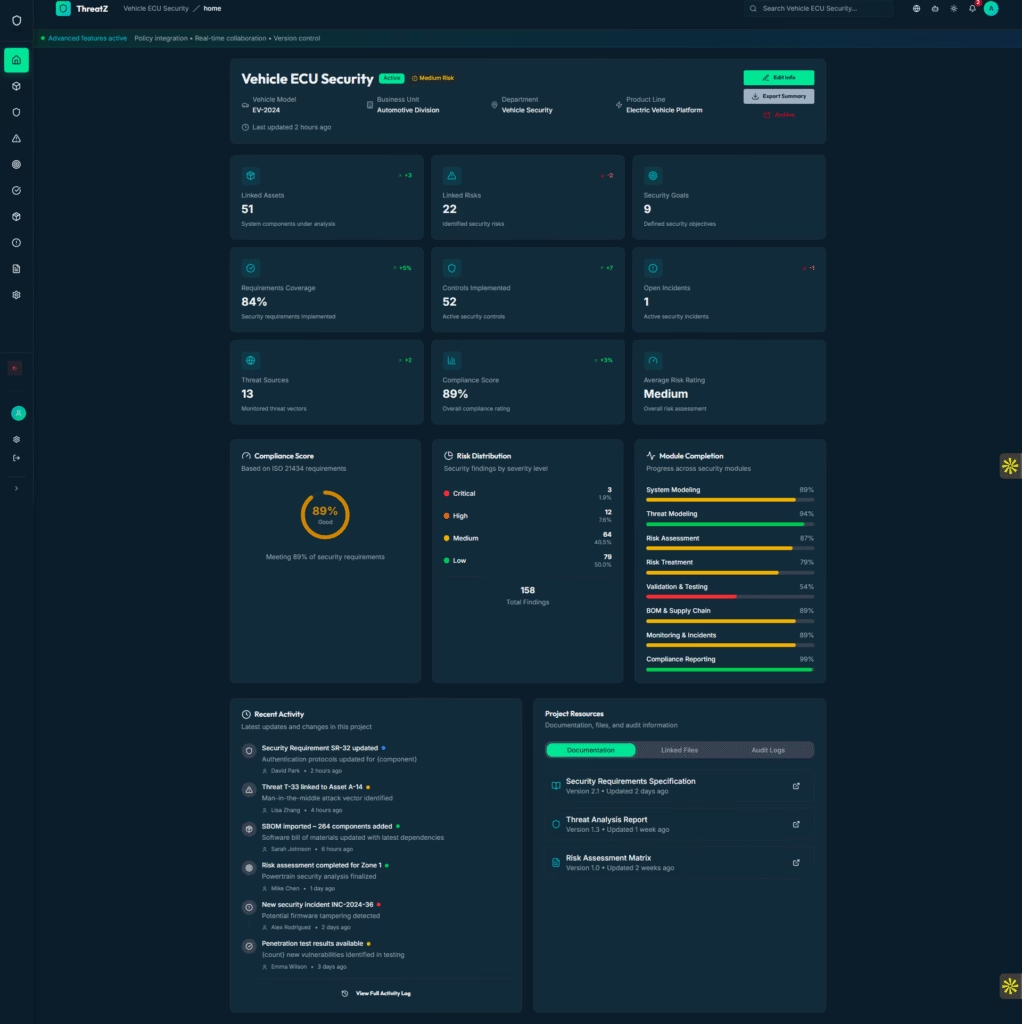
lower cost of ownership
We reduce total ownership costs through efficient, reliable solutions that deliver long-term value.
Maintatin trust
Build and preserve customer confidence by demonstrating your commitment to protecting their data.
Prevent Financial Loss
Avoid costly data breaches and system downtime that can impact your bottom line.
Ensure Compliance
Meet regulatory requirements and industry standards for data protection and privacy.

