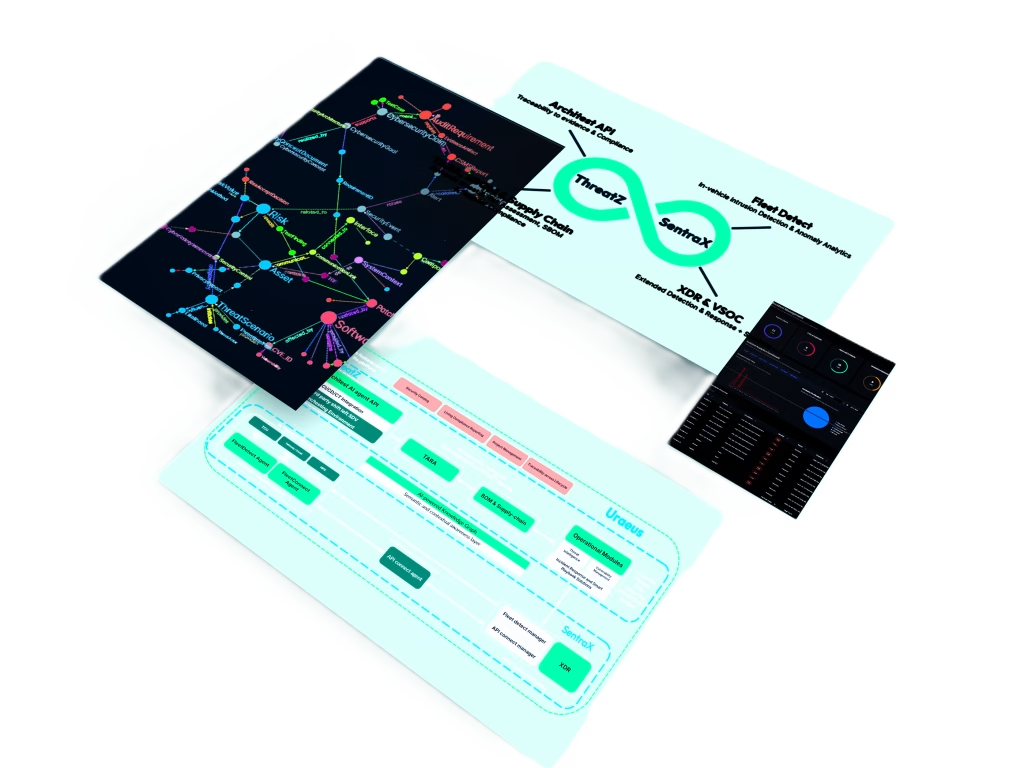
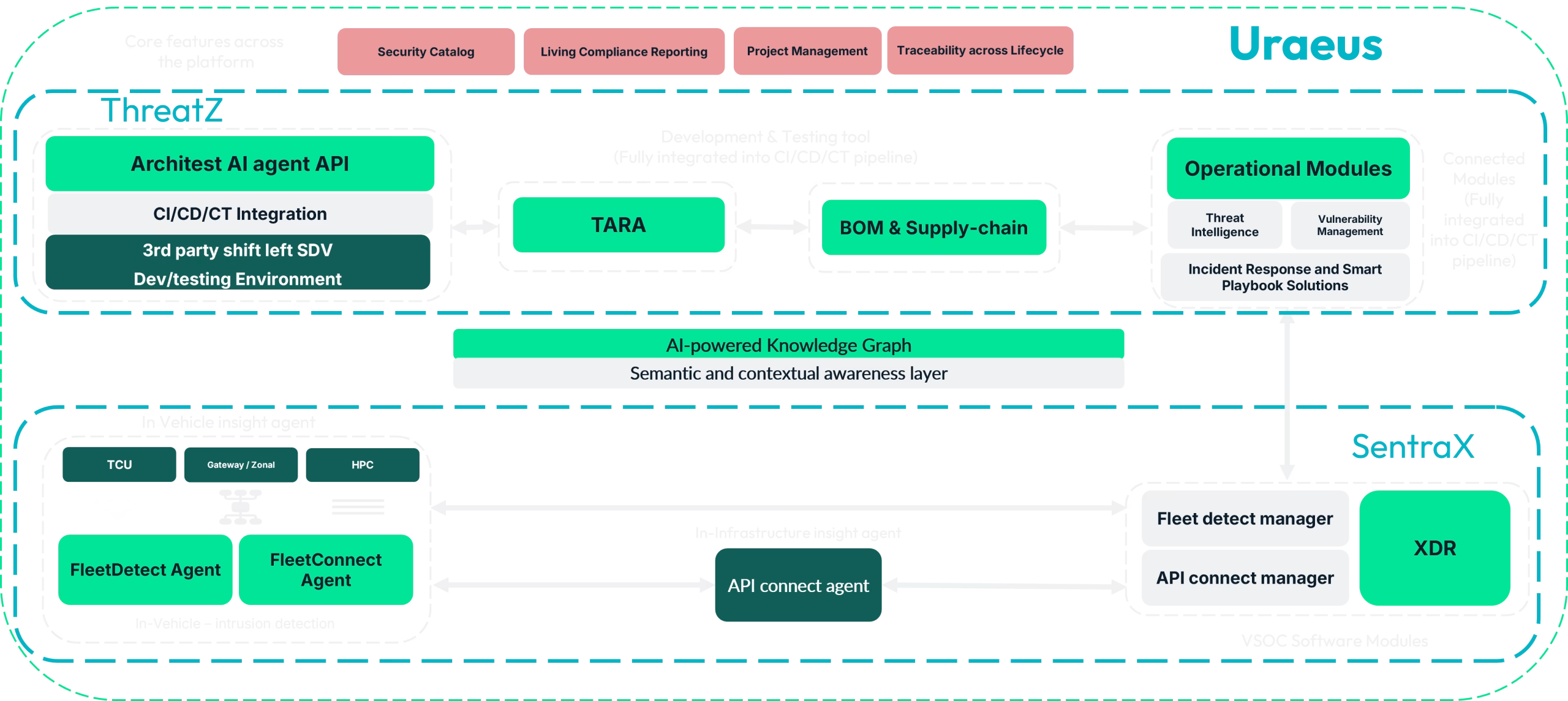
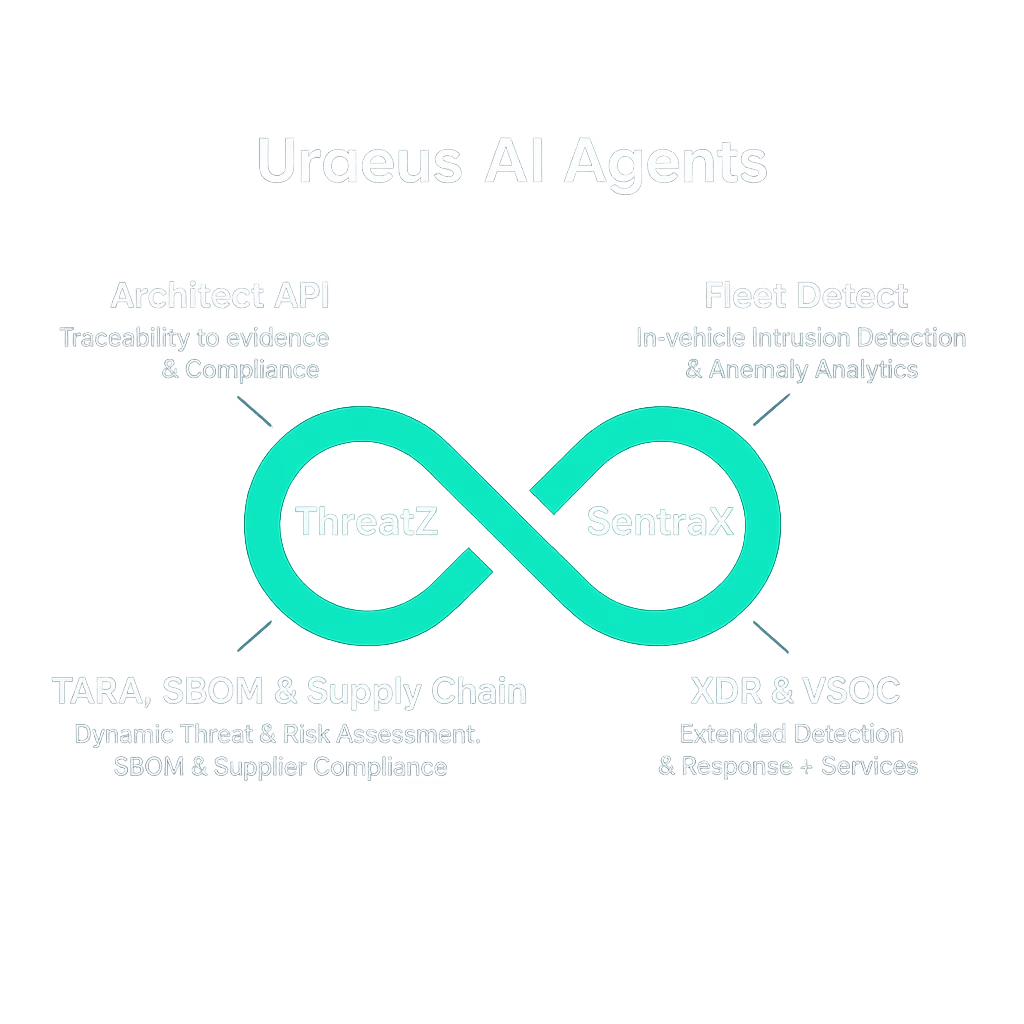
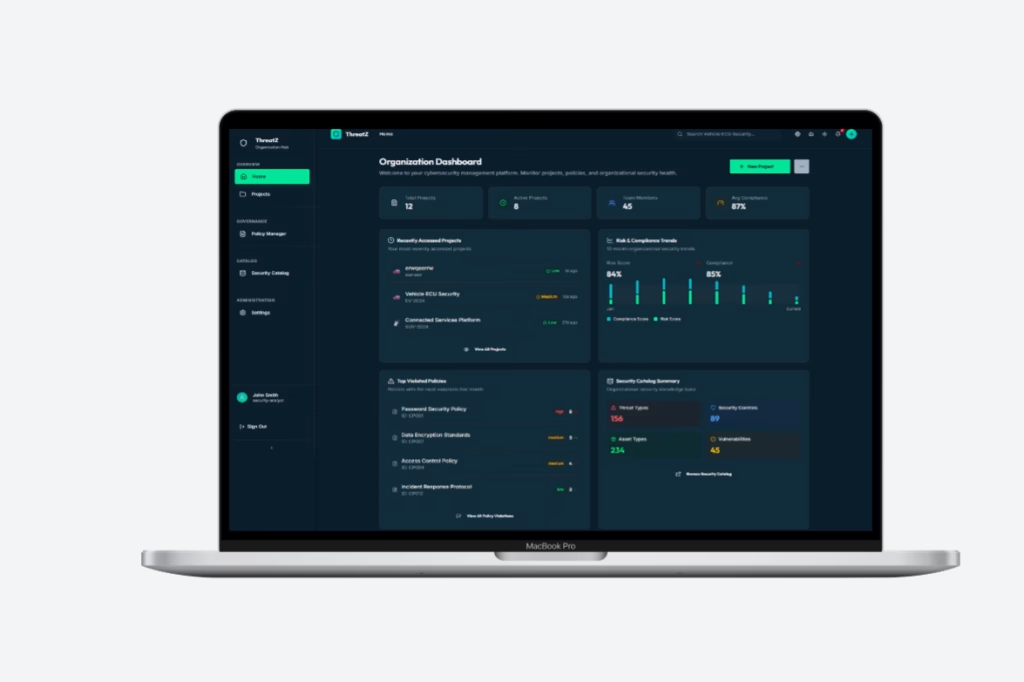
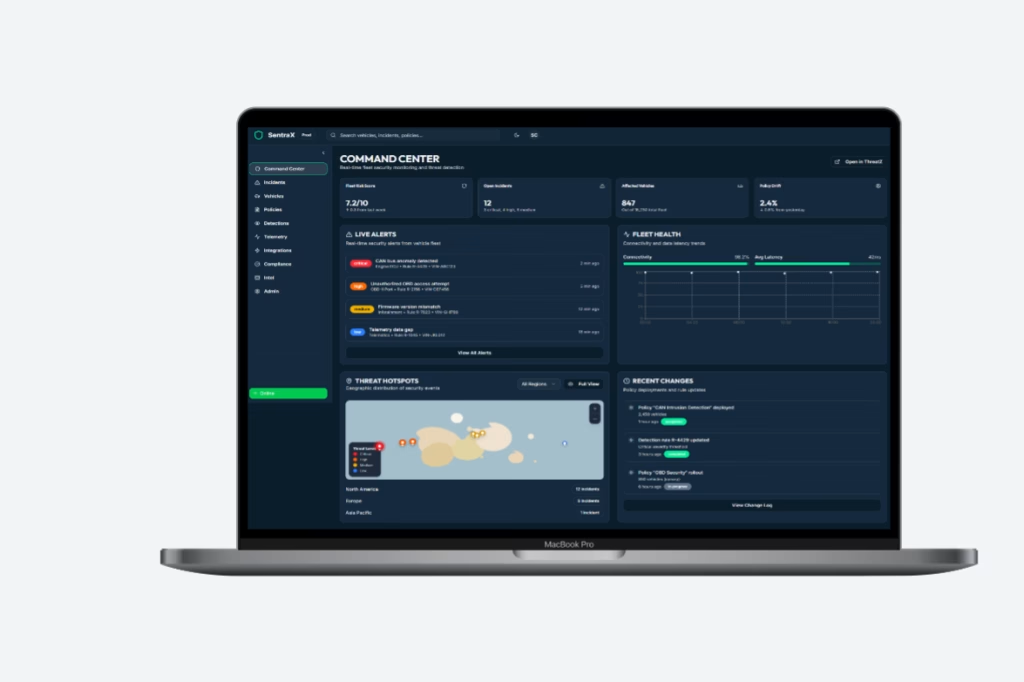
Uraeus – AI-Powered Automotive Security Platform
Uraeus unifies CSMS, in-vehicle IDPS and XDR in one automotive security platform. It bridges development and operations, helping OEMs and suppliers meet ISO 21434 and UNECE R155 while enabling real-time detection and response across vehicles and fleets.