ThreatZ is an automotive CSMS platform built for Tier-1 suppliers, ECU manufacturers and automotive software providers. It centralizes TARA, SBOM, vulnerabilities, incidents and compliance reports in one place. This helps suppliers manage cybersecurity across multiple OEM programs and prove ISO 21434 / UNECE R155 compliance with far less manual effort.
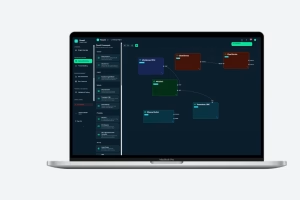
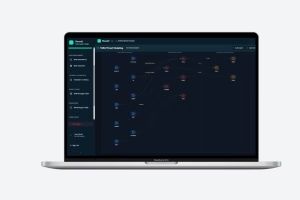
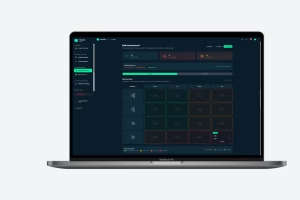
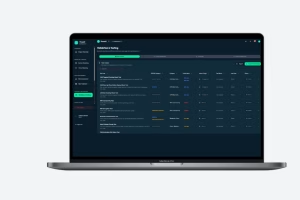
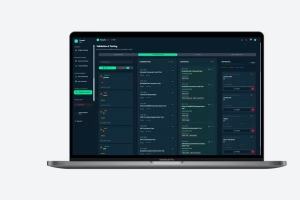
ThreatZ structures your threat analysis and risk assessment (TARA), links it to security goals, requirements and controls, and stores all evidence in a traceable CSMS. It includes report templates for ISO 21434 work products and UNECE R155 documentation, so you can generate consistent reports per project. Because TARA, SBOM, incidents and tests are all linked, auditors can easily follow the full cybersecurity trail.
The Starter license is for pilots and single product lines, and includes the Foundation + TARA modules. Pro adds the full BOM & Supply Chain module for SBOM and vulnerability management across several OEM programs. Enterprise includes all modules, including Operations, and is designed for full CSMS deployments with advanced integrations, flexible deployment options and dedicated support.
Yes. ThreatZ is designed to co-exist with OEM portals and internal tools, not replace them. It integrates with common architecture and ALM tools (such as Enterprise Architect, Simulink, Polarion, PTC, JIRA) and test environments like CANoe and ECU-Test. Through REST APIs, webhooks and exports, ThreatZ can act as the knowledge graph backend while your existing portals remain the user-facing front-end.
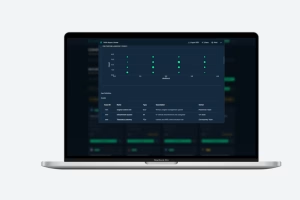
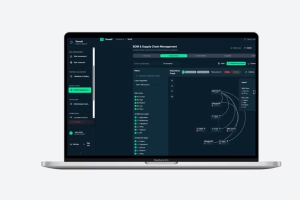
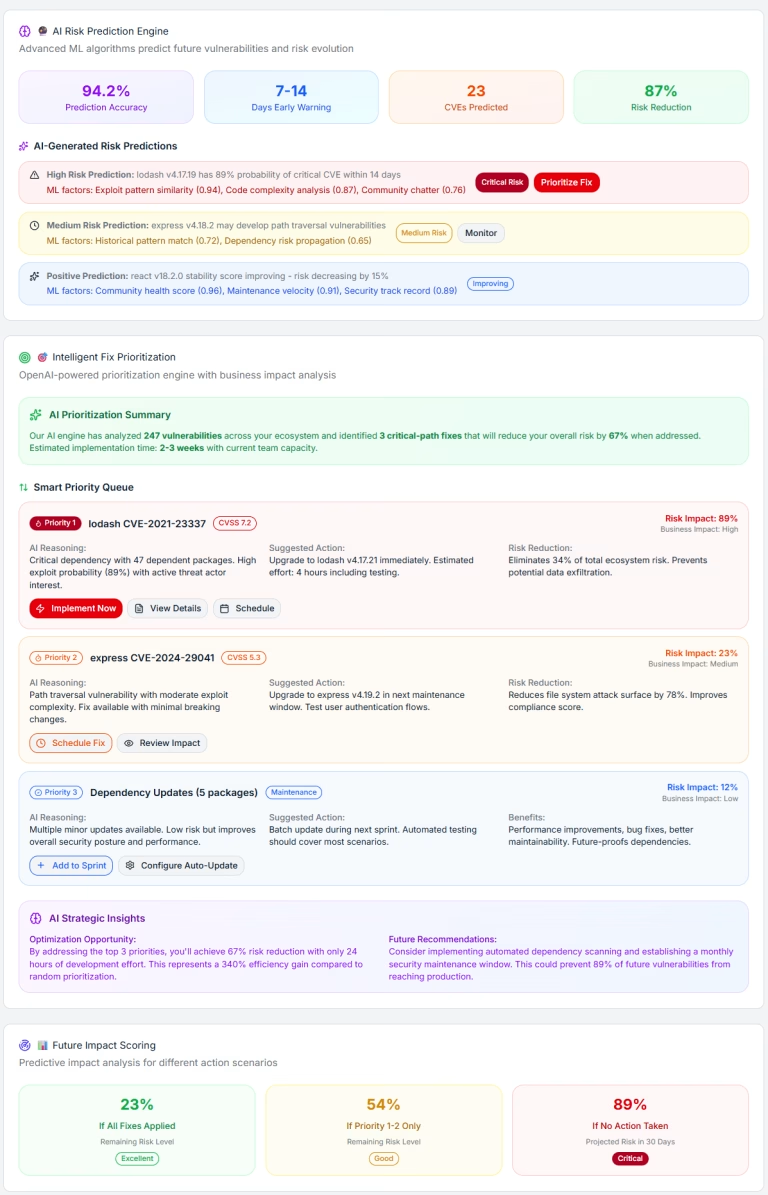
With the BOM & Supply Chain module, ThreatZ manages SBOMs per ECU, software product and vehicle platform, including dependencies and versions. It ingests vulnerability data from sources like NVD, OSV and CISA, maps CVEs to your components and links them to risks, mitigations and suppliers. This gives you an automotive-focused SBOM and vulnerability management solution directly inside your CSMS.
ThreatZ supports SaaS (cloud-hosted), private cloud and on-premise / air-gapped deployments. SaaS is best for fast rollout with managed infrastructure. Private cloud lets you run ThreatZ in your own Azure/AWS/GCP environment under your security policies. On-premise and air-gapped options are tailored for highly sensitive or regulated automotive projects that require full control over data.
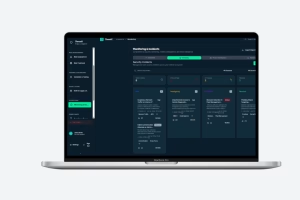
Yes. Many automotive companies already have internal CSMS portals or workflows. ThreatZ can sit behind these systems as the central cybersecurity knowledge graph, connecting TARA, SBOM, vulnerabilities and incidents. This lets you keep your existing processes and UI, while replacing fragile spreadsheets and custom scripts with a robust platform that scales across OEMs and programs.
Most customers can start a ThreatZ Starter pilot in a few weeks. We typically begin with one product line or ECU, migrate existing TARA or SBOM data, and configure templates to match your OEM and ISO 21434 requirements. From there, teams usually reach a first “aha moment” within a few TARA sessions, once they see everything linked in a single CSMS.