Introduction
In an era of increasing digital connectivity and the ubiquitous transfer of sensitive information, the Transport Layer Security (TLS) protocol has emerged as a fundamental cornerstone of secure communication. TLS provides a secure and reliable channel for transmitting data over a network, ensuring confidentiality, integrity, and authenticity. This technical article aims to demystify the TLS protocol, delving into its inner workings and exploring its essential role in safeguarding data in today’s interconnected world.
Understanding TLS
Transport Layer Security (TLS) is a cryptographic protocol designed to establish a secure communication channel between two entities over a network. It operates at the transport layer of the network stack, sitting on top of lower-level protocols such as TCP/IP. TLS ensures secure communication by encrypting data, authenticating entities, and protecting against eavesdropping, tampering, and impersonation attacks.
Key Components of TLS
1- Handshake Protocol:
The TLS handshake protocol is responsible for establishing a secure connection between the client and server. It consists of the following steps:
- Client Hello: The client initiates the handshake by sending a Client Hello message to the server. This message includes the TLS version supported by the client, a random value called the “client random,” and a list of supported cipher suites.
- Server Hello: The server responds with a Server Hello message, selecting the TLS version, cipher suite, and a server random value. The server may also send its digital certificate for authentication.
- Certificate Exchange: If the server sends a digital certificate, it contains the server’s public key and is used to verify the server’s identity. The client checks the certificate’s validity and authenticity using trusted Certificate Authorities (CAs).
- Key Exchange: During this step, the client and server agree on a key exchange algorithm to securely exchange session keys. This ensures that the session keys used for encryption and decryption are securely established.
- Authentication and Key Agreement: The client and server perform mutual authentication using their private and public keys, respectively. This ensures that both parties are who they claim to be.
- Session Key Generation: Based on the agreed-upon key exchange algorithm, the client and server independently generate session keys that will be used for symmetric encryption and decryption during the session.
- Finished: To conclude the handshake, both the client and server send Finished messages. These messages contain a hash of all previous handshake messages, ensuring the integrity of the handshake process.

2- Record Protocol:
The TLS record protocol operates on top of the established secure connection and is responsible for fragmenting, encrypting, and authenticating data exchanged between the client and server.
- Fragmentation: The record protocol breaks the data into manageable chunks called “records.” Each record typically corresponds to a single application-layer protocol message. If the data to be transmitted is larger than the maximum record size, it is fragmented into multiple records.
- Encryption: Before transmission, the record protocol encrypts each record using symmetric-key encryption. The encryption algorithm is determined during the handshake phase. Common encryption algorithms include Advanced Encryption Standard (AES) and Triple Data Encryption Standard (3DES).
- Authentication and Integrity: The record protocol ensures the integrity of transmitted data by appending a Message Authentication Code (MAC) or a cryptographic hash to each record. This ensures that the data remains unchanged during transmission and detects any tampering attempts.
3- Cipher Suites:
Cipher suites define the cryptographic algorithms used for key exchange, encryption, and authentication during the TLS handshake. They encompass the following components:
- Key Exchange Algorithm: The key exchange algorithm determines how the client and server agree on session keys securely. Common key exchange algorithms include RSA, Diffie-Hellman (DH), and Elliptic Curve Diffie-Hellman (ECDH).
- Encryption Algorithm: The encryption algorithm determines how the data is encrypted using symmetric-key encryption. Common encryption algorithms include AES, 3DES, and ChaCha20.
- Message Authentication Code (MAC) Algorithm: The MAC algorithm generates a code that ensures the integrity and authenticity of transmitted data. Common MAC algorithms include HMAC-SHA256 and HMAC-SHA384.
- Hash Function: The hash function is used for various purposes, including generating digital signatures, creating cryptographic hashes for data integrity, and deriving session keys. Common hash functions include SHA-256 and SHA-384.
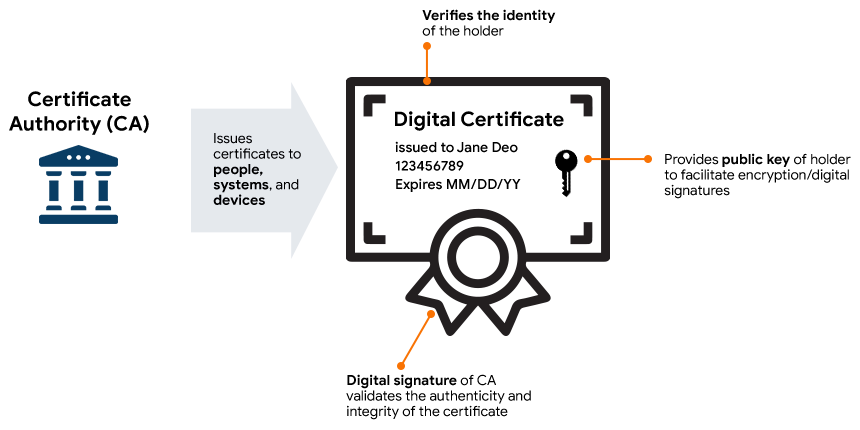
4- Digital Certificates:
TLS relies on digital certificates to establish trust and verify the authenticity of entities involved in the communication. Digital certificates contain the following information:
- Public Key: The digital certificate contains the public key corresponding to the private key used for encryption and digital signatures.
- Entity Information: The certificate includes information about the entity, such as its name, organization, and website.
- Certificate Authority (CA) Signature: The digital certificate is signed by a trusted Certificate Authority (CA) to vouch for its authenticity. The CA’s signature ensures that the certificate has not been tampered with.
Benefits of TLS:
- Data Confidentiality: TLS encrypts data before transmission, ensuring that only authorized recipients can decrypt and access the information. This prevents eavesdropping and protects sensitive data from being compromised.
- Data Integrity: TLS employs cryptographic hashes to verify the integrity of transmitted data. This ensures that data remains unchanged during transmission, protecting against tampering or unauthorized modifications.
- Authentication: TLS leverages digital certificates to authenticate the identities of communicating entities. This prevents impersonation attacks and establishes trust between the client and server.
- Trust and Privacy: By using trusted digital certificates and encryption, TLS enhances user trust in online transactions, protects privacy, and safeguards against malicious activities.
Conclusion
In the automotive industry, the TLS protocol serves as a linchpin in securing ECU communication. By encrypting data, enabling authentication, and ensuring data integrity, TLS enhances the security and reliability of ECU communication. Robust implementation of TLS protocol strengthens the automotive ecosystem, protecting critical operations, safeguarding sensitive data, and fostering trust in connected vehicle environments.